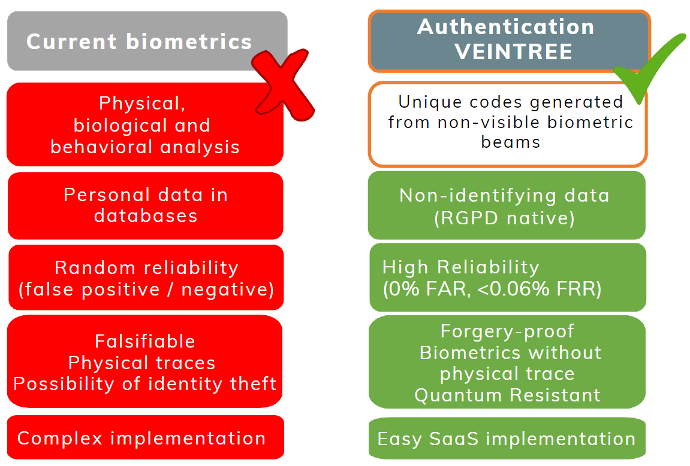
A unique and specific authentication code
The
result of the scan of your palm is a unique and specific authentication code,
unique to you, whose starting point is your hand.
In other words, your hand is
the key to the whole process. You don't need to present anything else to be
authenticated.
Authentication is based on a physical form (the inside of your hand) and requires no personal identification per se (if this is not necessary)
No
reference databases are used,
no image comparison are made,
no biometrics are
archived.
The Veintree authentication system quickly observes your palm, captures and analyzes the image and biometric flows of your vein network, and uses the data from this temporary reading to activate calculation algorithms developed by Veintree.
Once
the biometric reading has served its purpose, it is immediately deleted to
protect your identity. Veintree's secure servers do not store any biometric
data.

Authentication is dissociated from identification
Normally,
as a basic principle, authentication is dissociated from identification.
However, for use cases or environments where personal identification is
required for authentication, this is an aspect and information managed
internally by the company or organization (governmental or otherwise) using the
Veintree authentication system, and not by Veintree itself.
Veintree's
role is solely to authenticate that you are an authorized person entitled to
the services corresponding to your request, access and transactions, not to
identify you. Our role is authentication, not identification.
Encryption without transmission of biometric data
Unique dynamic coding and encryption are calculated locally on the device used. This encrypted result is communicated to Veintree servers installed at customer sites, which analyze the unique code received and accept or reject the authentication. In all cases, the infrared image of your hand and the biometric data captured are destroyed immediately after the encrypted code is generated, ensuring the person's anonymity.
Even the code itself is eliminated, since it
is designed for one-time use only


Sunlight as multi-spectral infrared illumination
In
practice, a smartphone camera, sensitive to certain infrared wavelengths, scans
your palm and captures the pattern of your vein network and its blood flow.
This sensing device may be a tablet-style device, a small device attached to
your cell phone, or possibly one built directly into most phones. When it's
sunny, natural light is sufficient, and there's no need to illuminate the palm.
Veintree
is the trusted third party and Web3 Oracle
that enables your digital transactions,
without
revealing your personal data.